Access Control and Intrusion Monitoring
Unauthorized Access Detection in Restricted Areas
When an unauthorized worker approaches or enters a designated security zone,
immediate detection and alerts proactively prevent violations of access regulations.
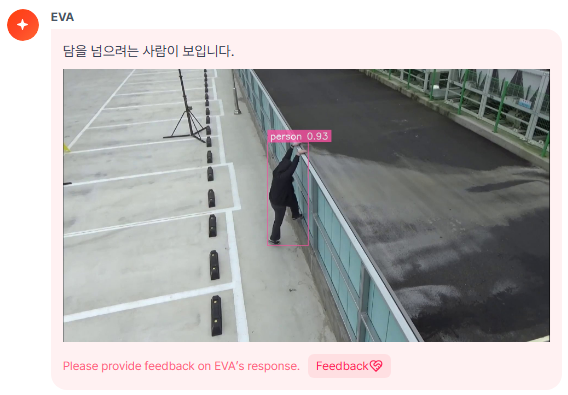
Obstacle Climbing Intrusion Detection
Real-time detection of abnormal approaches, such as climbing over physical barriers like walls or fences,
supports immediate response by security personnel in the event of external intrusion.
Suspicious Activity and Loitering Detection
Automatic identification of abnormal behavior such as repetitive loitering or lingering around the facility,
allowing for early identification of potential security threats and provision of pre-emptive warnings.
The Process of Turning a Regular Camera into an AI Camera in Just 5 Minutes!

Detection Scenario Configuration
Easily write detection conditions using prompts.
Example: "Detect a person climbing over a wall"
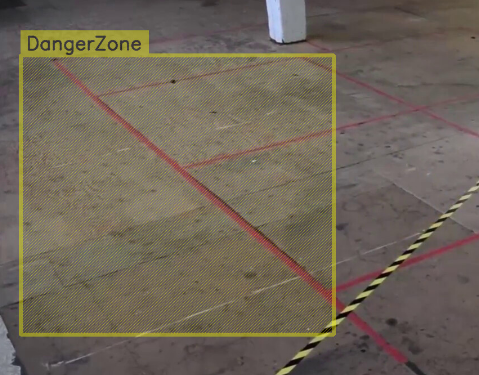
Zone Configuration
Set the zone for the restricted area.
Detection will be performed within this specific zone.
Result Check & Optimization
Check the detection results and
modify the zone and scenario if necessary.
Proactive Security Threat Prevention
Intrusion into industrial facilities can cause significant damage,
including theft, equipment damage, and operational shutdowns.
EVA ensures real-time monitoring of restricted area access control and intrusion situations,
allowing for early identification of risk factors and establishment of a rapid response system.
Automated Response via Security System Integration
EVA goes beyond simple video monitoring, integrating with access gates, alarm devices, and lighting control systems.
It executes immediate automatic security measures such as blocking, alarming, and tracking upon intrusion.
This realizes a Physical Security environment that strengthens facility safety.
